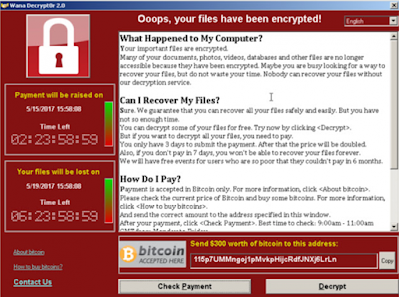
You might be familiar with the image shown above. The locked computer device with a pop up asking for a ransom to unlock the device. This is what Ransomware or Ransom Malware is.
Image Source:ISEA
Ransomware is a malicious application that employs cryptography techniques to hold control of the victim's PC. A ransomware encrypts and locks the legitimate user's access to the computer system, and in exchange to decrypt data, the attacker demand ransom in the form of cryptocurrency, like Bitcoin.
The malware hostage the victim’s personal files, although the files remain on the device but are inaccessible by the user. In most cases, a time is given to the victim to pay the ransom and get the unlock key, or the device will be locked permanently.
How Ransomware Works?
The ransomware and many other malware are generally distributed via a flooding spam mails or targeted attack. The malware needs an attack vector to establish its presence in the end device. Once the presence is established, the malware starts exploiting and deploying a malicious binary in the infected machine.
Ransomware uses the asymmetric encryption method. This method includes using two keys, i.e., public-private key pair- one to encrypt file and the other to decrypt it. The attacker generates the key pair and provides the private key for decryption only if the victim pays the ransom. Without the private key, it is almost impossible to break the encryption.
“Kaspersky security experts have been able to decrypt hijacked data, but they admit it isn’t always possible if the encryption is very strong, as is the case with CryptoLocker.”
(Source:Kaspersky)
The ransomware is designed so that it spreads rapidly in the network and affects the databases and file servers. The files are encrypted. Ransomware prompt to pay under 24 or 48 hours to decrypt the files; else, they are lost forever.
Ransomware Timeline
Ransomware is not a fancy term; it has been in action since the 1980s and has been evolving. Initially, when ransomware targeted individuals, it now targets big businesses to yield a more significant amount. Some notable ransomware in history are as-
- PC Cyborg (Also known as AIDS Trojan) in the late 1980s: The first-ever known ransomware, released by AIDS researcher Joseph Popp. He distributed 20,000 floppy disk of containing malware to other AIDS researchers, and very few of them knew that the malware would lock the C drive after 90 reboots and ask to renew the license by paying $189 by mail to PC Cyborg Corp.
- GpCode in 2004: The malware implemented a weak form of RSA encryption on the victim's machine for ransom.
- WinLock in 2007: The malware was different from all others, so that instead of encrypting the data, it locked victim out of the desktop and displayed pornographic images on the desktop. Victims need to pay for removing the photos.
- Reveton in 2012: This “so-called law enforcement” ransomware locked the victim's PC and displayed a real-looking fake screen from a law enforcement agency. The message stated the victim has committed some crime and told them to pay the fine via a prepaid card.
- CryptoLocker in 2013: CryptoLocker ransomware used the military-grade encryption that used the remote server to store the key required for decryption. The attack infiltrated about 250,000 systems and reaped $3 million before taken offline.
- Locky in 2016: The malware includes the social engineering tactics to deliver itself via a mail, which consists of a Microsoft Work document attachment, which looks like some bill to be paid. But it was a malicious macros. The ransomware has evolved so much that it can use JavaScript files, which cannot be even detected by anti-malware products.
- WannaCry in 2017: The ransomware WaanaCry in May 2017 and Petya in June 2017 was the encryption ransomware, which anonymously spread between computers.
- Sodinokibi in 2019: The cybercriminals used the managed service providers (MSP) like dental offices to spread infection.
Are Mobile Devices SAFE from Ransomware?
It’s a clear-cut answer--- NO.
After the CryptoLocker, the ransomware was seen on an extensive scale in mobile devices. Mobile ransomware is delivered via a malicious mobile app. The malware displays a message that the device has been locked due to some illegal activities. Also, the message conveyed that the device will unlock once the fee is paid. To regain access to the mobile device, it was required to boot the machine in safe mode and remove the infected app.
Types of Ransomware
There are various types of ransomware which differ on the harm causing intensities, some are more harmful while some are less, but they all have one thing in common- a ransom. Some of the ransomware types are:
- Crypto Malware: These types of malware encrypt the victim's personal files, folders, and hard-drives and are considered as the most harmful. The 2017 WannaCry ransomware attack is a well familiar example.
- Lockers: These types of ransomware are designed for infecting the operating system and make victim lockout of all computer resources and files.
- Scareware: Scareware is a malware that plays with human's fear. It scares the user by claiming that viruses are found or slow system performance and force the user to download an antivirus application, which in reality is ransomware.
- Doxware: Also known as leakware or extortionware. As the name suggests, these ransomware threatens the victim to publish the stolen information if ransom is not paid.
- RaaS: You must have heard of SaaS, IaaS, PaaS in cloud computing, but RaaS is not related to that. It stands for ‘Ransomware-as-a-Service’. It is a type of malware anonymously hosted by the hacker but is purchased or rented by anyone. The cybercriminals manage everything- from deployment to collect payment and decryption of the files.
- Mac Ransomware: KeRanger, in 2016, affected the Apple user systems through an app called ‘Transmission.’
- Mobile Ransomware
Get to know about general MALWARE
Defend Against Ransomware
“Geographically, ransomware attacks are still focused on western markets, with the UK, US, and Canada ranking as the top three countries targeted, respectively.”
Source: Malwarebytes
Still, everyone needs to be aware of the threats and the solutions to mitigate such risks. Some of the steps that can prevent an individual as well as an organization against such attacks:
- Do Regularly Backup Data: The data backup must be taken periodically and must be kept somewhere out of reach from the company’s network, preferably on cloud or external hard-drives, which in case of attack will not affect the backup copies and it could be used to restore files.
- Do Use Security Software: Always use original security software like Anti-malware software, IDS/IPS and keep them updated.
- Don’t Enable Automatic Email Opening: Since the malware is mostly spread through the email, it is necessary to be careful while opening any mail. Disable the automatic mail opening system.
- Don’t Click on Suspicious Links: While surfing online or in received messages or emails, be aware of the links you are opening. Never open any suspicious link obtained from a Phishing Mail or any pop-up on the site.
- Use Cloud Services: Cloud services provide extraordinary features in case of disaster recovery and allow to “roll back” the system to the earlier state.
- Do Use Only Secure Networks: Never use public Wi-Fi as they are not secure, and the bad guys always snoop around the internet usage and can deploy a malicious code with its help. Consider using a VPN instead while on a public network.
What if I'M UNDER ATTACK?
Anyhow, if you become the victim of a ransomware attack, the first thing to keep is Calm. Keep calm and watch for the best possible chances to minimize damage and return to normal:
- Isolate the infected devices from all other devices in the network.
- Disconnect the internet to prevent the spread of the malware.
- Assess the damage, try to identify Patient Zero.
- Identify the ransomware you are dealing, with the help of a worldwide initiative- No More Ransom.
- Don’t pay the ransom, as even after that, there is no guarantee that the files will be unlocked.
- Immediately inform about the attack on the law enforcement agencies.
- Research for the decryption options as several free decryption keys can be found in No More Ransom.
- When in the disaster recovery phase, firstly scan all systems with an anti-malware application and then evaluate backups to restore files.
- Start from Scratch is what you are left with in the last.
Every day a new variant of ransomware is appearing. It's good or say better to remain informed and aware of the possible threats, damages, dos, and don’ts so that you can minimize your exposure towards the attacks. It can help you keep your files, databases, information, and yourself safe from the “BAD GUYS.”
"...REMAIN VIGILANT, REMAIN SECURE..."